Stop Known Threats.
Anywhere and Everywhere.
One security solution for every device and network.
With threatER
threatER in Action
Detect
Harness massive data streams from threatER and your tools to instantly detect threats
Eliminate
Use data to identify and block malicious and unknown entities
Secure
Work with your existing stack to continuously update your security posture and keep you protected in real-time
Threats Blocked Yesterday
3.6 BillionThreats Blocked Last 7 Days
Why threatER Stands Out
Key Benefits:
How threatER Enforce Works
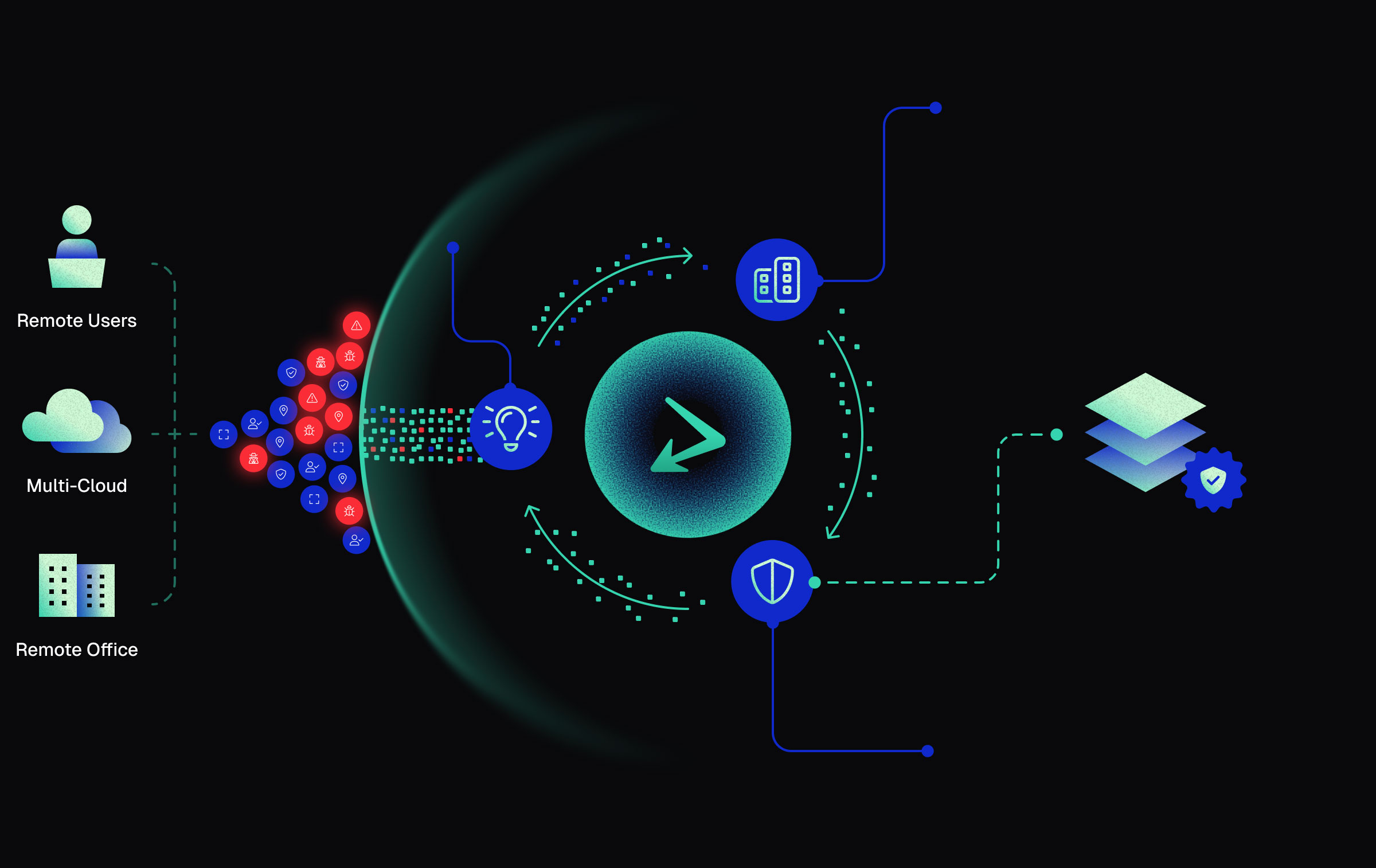
Use Segmentation to Reduce Your Problem Space
Purposefully allow trusted traffic, deny untrusted traffic and allow the remaining traffic to pass through to your other security controls.
Gain Better Insights From Your Reduced Problem Space
Cut through the noise with fewer false positives, reduced alert volume, and less data strain on downstream tools.
Feed Those Additional Insights Back Into threatER
Automate feedback with a simple API call – seamlessly reinforcing trust by turning every detection into smarter, system-wide protection.
Who It’s For

Small Businesses
Easy-to-deploy protection
Enterprises
Scalable security for complex networks

MSPs
Managed security with minimal overhead

Remote Workforces
Seamless protection on any device
Join Thousands Securing
Their Business with threatER
Before threatER, we were taking in public and government feeds but didn’t have the room for industry-specific feeds, Webroot / DomainTools, or what we examined through our own malware analysis.
The product is easy to use, requires very little maintenance and is essential for a multi-layered security approach.
Everyone should have this tool. It is simple to use and should be in everyone’s security stack. threatER has saved us from breaches.
threatER as that first line of defense has completely transformed our network. Before threatER, we were seeing an overwhelming amount of failed log in attempts. Since putting threatER in, those attempts have drastically decreased. This has freed up our time to focus on other security priorities.
Having theatER deployed inline between the internet & our firewall allows us to take a load off the firewall from a threat intelligence perspective and frees up resources for the firewall to do faster SSL inspection
My network guys are happy that we put threatER in place – threatER blocks 1.1B threats per month that don’t hit the firewall resulting in firewall CPU & memory utilization efficiencies.
We use Meraki and threatER. And we would never consider using Meraki without threatER being in front of them. It would impossible to manage and nowhere near secure.
Before threatER, we were taking in public and government feeds but didn’t have the room for industry-specific feeds, Webroot / DomainTools, or what we examined through our own malware analysis.
The product is easy to use, requires very little maintenance and is essential for a multi-layered security approach.
Everyone should have this tool. It is simple to use and should be in everyone’s security stack. threatER has saved us from breaches.
threatER as that first line of defense has completely transformed our network. Before threatER, we were seeing an overwhelming amount of failed log in attempts. Since putting threatER in, those attempts have drastically decreased. This has freed up our time to focus on other security priorities.
Having theatER deployed inline between the internet & our firewall allows us to take a load off the firewall from a threat intelligence perspective and frees up resources for the firewall to do faster SSL inspection
My network guys are happy that we put threatER in place – threatER blocks 1.1B threats per month that don’t hit the firewall resulting in firewall CPU & memory utilization efficiencies.
We use Meraki and threatER. And we would never consider using Meraki without threatER being in front of them. It would impossible to manage and nowhere near secure.