Real-Time, Automated Threat Protection Eliminate Threats at the Source
Included premium integrations:
Immediate Protection.
Delivered Anywhere
You Need It
On-Premises
Defend critical infrastructure with seamless, high-performance threat protection built for scale.

Remote & Hybrid Teams
Keep your distributed workforce secure—without relying on slow, complex VPN setups.

Cloud & Edge
Extend enforcement to wherever your data lives, from cloud workloads to the edge.
Wi-Fi Networks
Bring security to the access point with built-in enforcement at the Wi-Fi layer—ideal for satellite offices, education, and SMBs.

Verdict API
Integrate threatER intelligence into your existing tools and platforms with real-time verdicts on IPs, domains, and threat actors—powering smarter decisions across your ecosystem.
How threatER Enforce Works
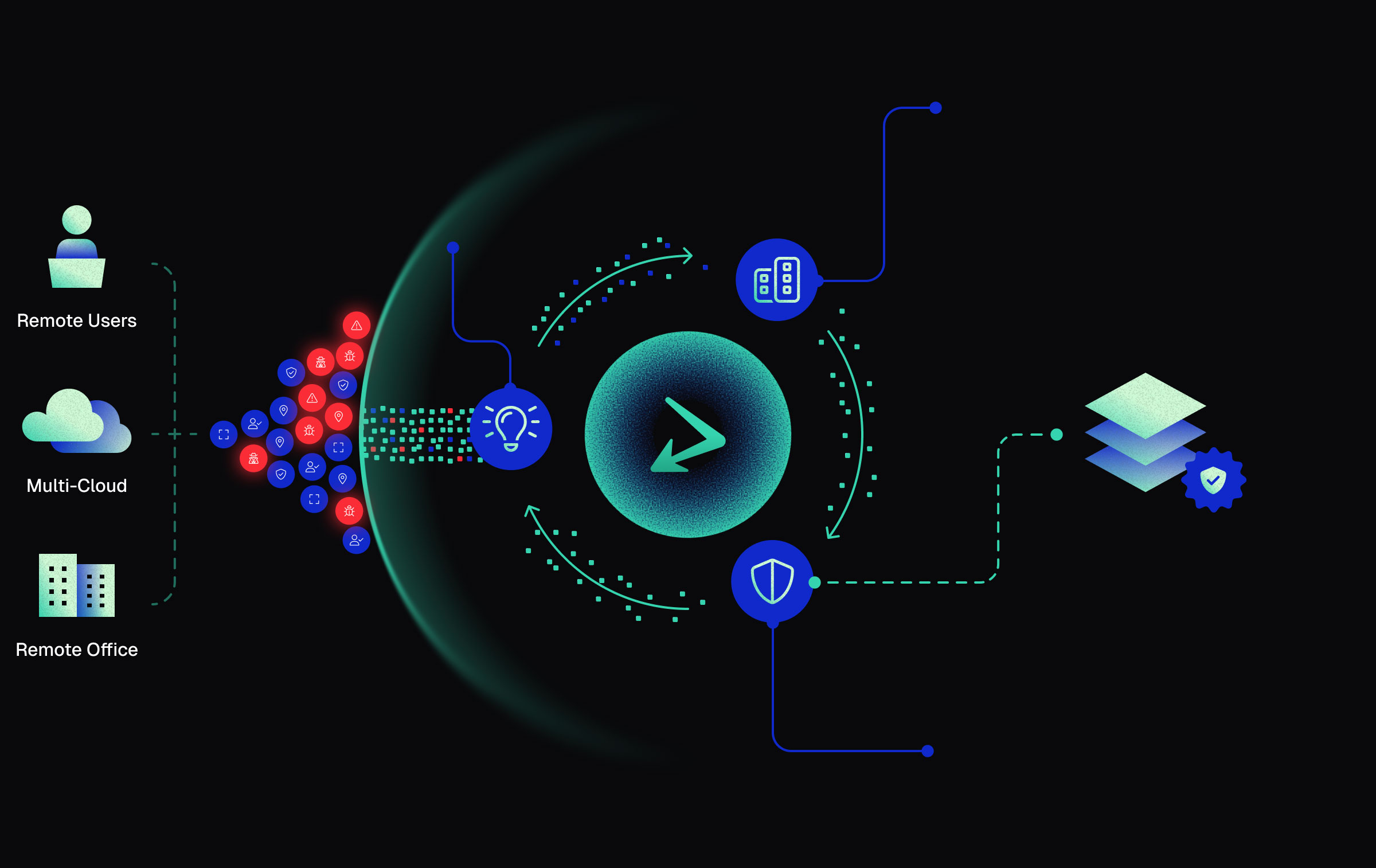
Use Segmentation to Reduce Your Problem Space
Purposefully allow trusted traffic, deny untrusted traffic and allow the remaining traffic to pass through to your other security controls.
Gain Better Insights From Your Reduced Problem Space
Cut through the noise with fewer false positives, reduced alert volume, and less data strain on downstream tools.
Feed Those Additional Insights Back Into threatER
Automate feedback with a simple API call – seamlessly reinforcing trust by turning every detection into smarter, system-wide protection.
Take Control of Your Security—Beyond the Limitations of Firewalls or Outdated Network Security Policies
threatER empowers you with 50+ seamless integrations and access to 30M+ real-time threat indicators, ensuring your security strategy is proactive, not reactive.

Effortless Integrations
Connect with leading data brokers and intel specialists.

Enhanced Intelligence
Gain access to premium cyber intelligence feeds with simple add-ons.

Streamlined Security Management
Easily extend protection through our Marketplace integrations.
Don’t let outdated firewalls limit your visibility—
upgrade to smarter, more adaptive security with threatER.
Why Choose threatER Enforce?
Pre-emptive Cybersecurity
Instead of waiting for threats to be detected, threatER Enforce actively prevents them from entering or leaving your network.
Designed for Modern Networks
Traditional security tools weren’t built for today’s distributed, cloud-first environments. threatER Enforce provides comprehensive protection across on-prem, cloud, and edge infrastructure.
Zero Performance Trade-Offs
Legacy firewalls and deep packet inspection can slow down your network. threatER Enforce works without latency, keeping your operations running at full speed.
Enforce can ingest and enforce on
up to 150 million threat indicators
at line speed and updates automatically.

Because Enforce does not rely on a single proprietary view of the threat landscape, it can ingest as much cyber intelligence as is available today in order to block traffic based on the best and most up-to-the-minute intelligence available.
No matter how threat actors are trying to get in, Enforce stops the call. This results in removing up to 30-50% of network traffic hitting your firewall and security stack.
Take Control of Your Network Security
Firewalls aren’t enough. Signature-based detection is too slow. threatER Enforce delivers real-time security, so you stay ahead of the attackers.
Ready to experience proactive threat blocking? Contact us today to learn more about deploying threatER Enforce in your environment.