©Threater 2024
Why Collect?
Gain a better understanding of the risks facing your organization
Unique cloud attackers list
Access to best-in-class cyber intelligence feeds and threat lists
Access to open source data
Compile and utilize up-to-the-minute intelligence for all your tools and technologies
Export Lists to your Firewall
Feed your firewall the intelligence it needs
Additional Features
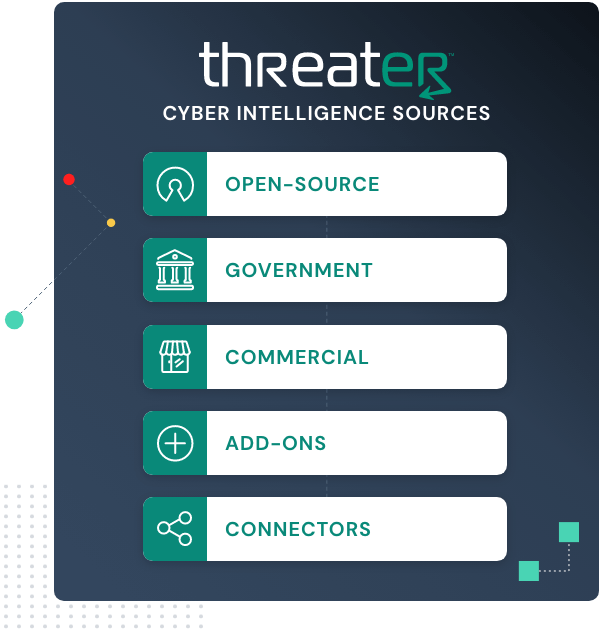
Don’t rely on one vendor’s view of the threat landscape for your cyber intelligence
- Source on near-unlimited cyber intelligence data by focusing on known threat actors
- Aggregate cyber intelligence from the entire community, including government agencies, open source organizations,
and private companies dedicated to gathering, analyzing,
and disseminating information about cyber threats, vulnerabilities, and activities.
Upgrade to ENFORCE
Block all known threats
Free Data Sources with Enforce Subscription

Millions of well-vetted malicious indicators of compromise (IOCs)

Millions of malicious domains and associated IP addresses

Known-good data (including Akamai, Amazon Cloudfront, Cisco Webex, Cloudflare, and more)
Looking for more?
Think of something that should be added to our Collect subscription?
Let us know here!