Firewall Gap #2: Limited Ability to Add Intelligence

In our previous blog, we took a closer look at the first firewall gap, which is that they don’t catch every threat. The main driver of this gap is that firewalls operate with too limited a view of threat intelligence. A logical way to close this gap is to add cyber intelligence into your firewall. However, while this sounds good in theory, as you will see it’s extremely challenging in practice. In this blog, we will focus on the second firewall gap – the limited ability to add threat intelligence into your firewall.
With a wide array of threat intelligence available, one thing an organization can do to fill the first firewall gap is to acquire additional threat feeds and integrate it into your firewall. This is a great idea but the challenge is firewalls have significant limitations using third-party threat feeds. The major limitation is the volume of third-party threat indicators a firewall can handle. However, there’s also another significant limitation on the ways you can integrate threat intelligence into the firewall.
External blocklists (also allow lists) are the key mechanism that allow you to add threat intelligence into the firewall. However, pretty much every firewall has significant limitations on the volume of indicators they can support in external blocklists.
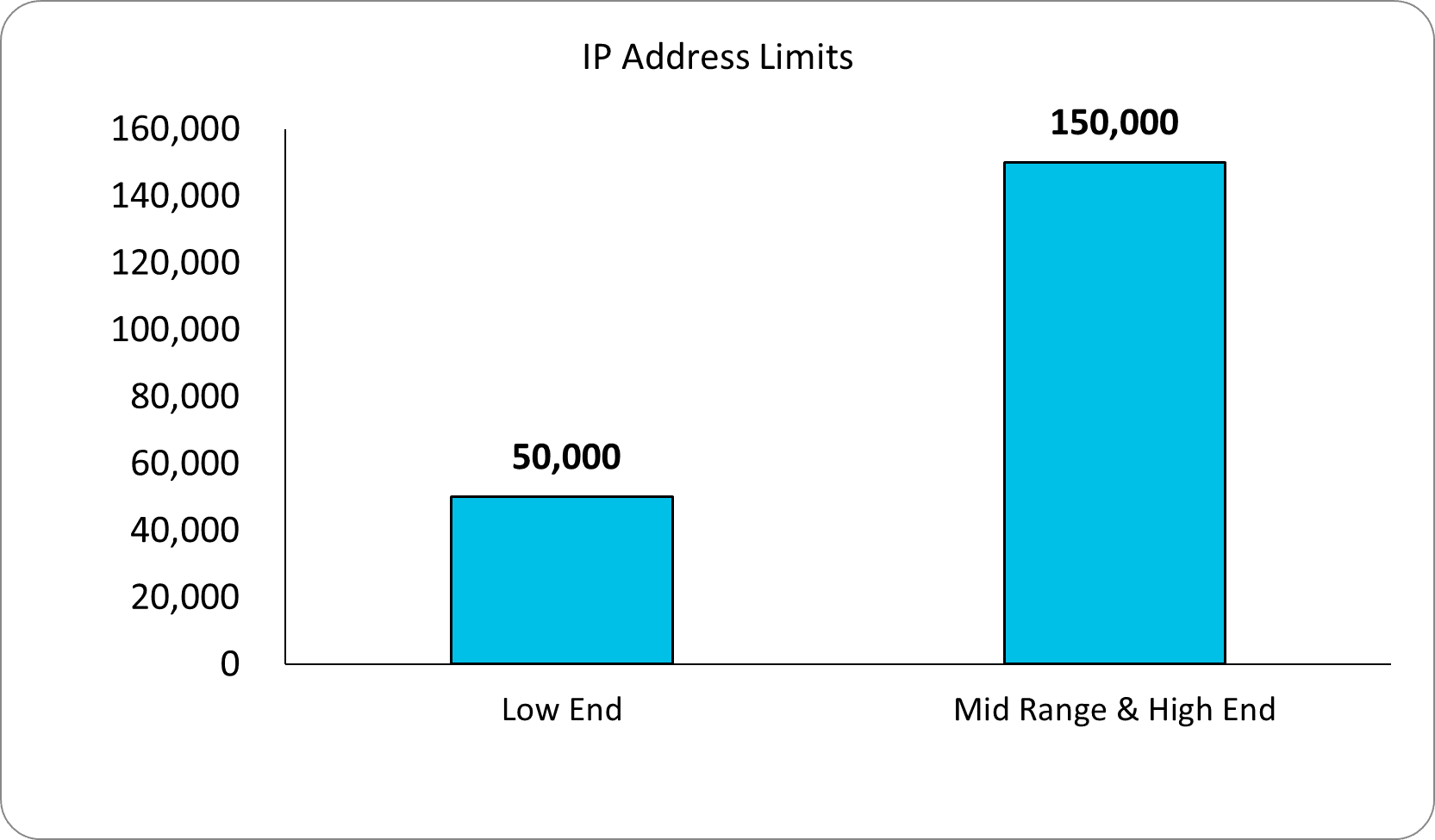
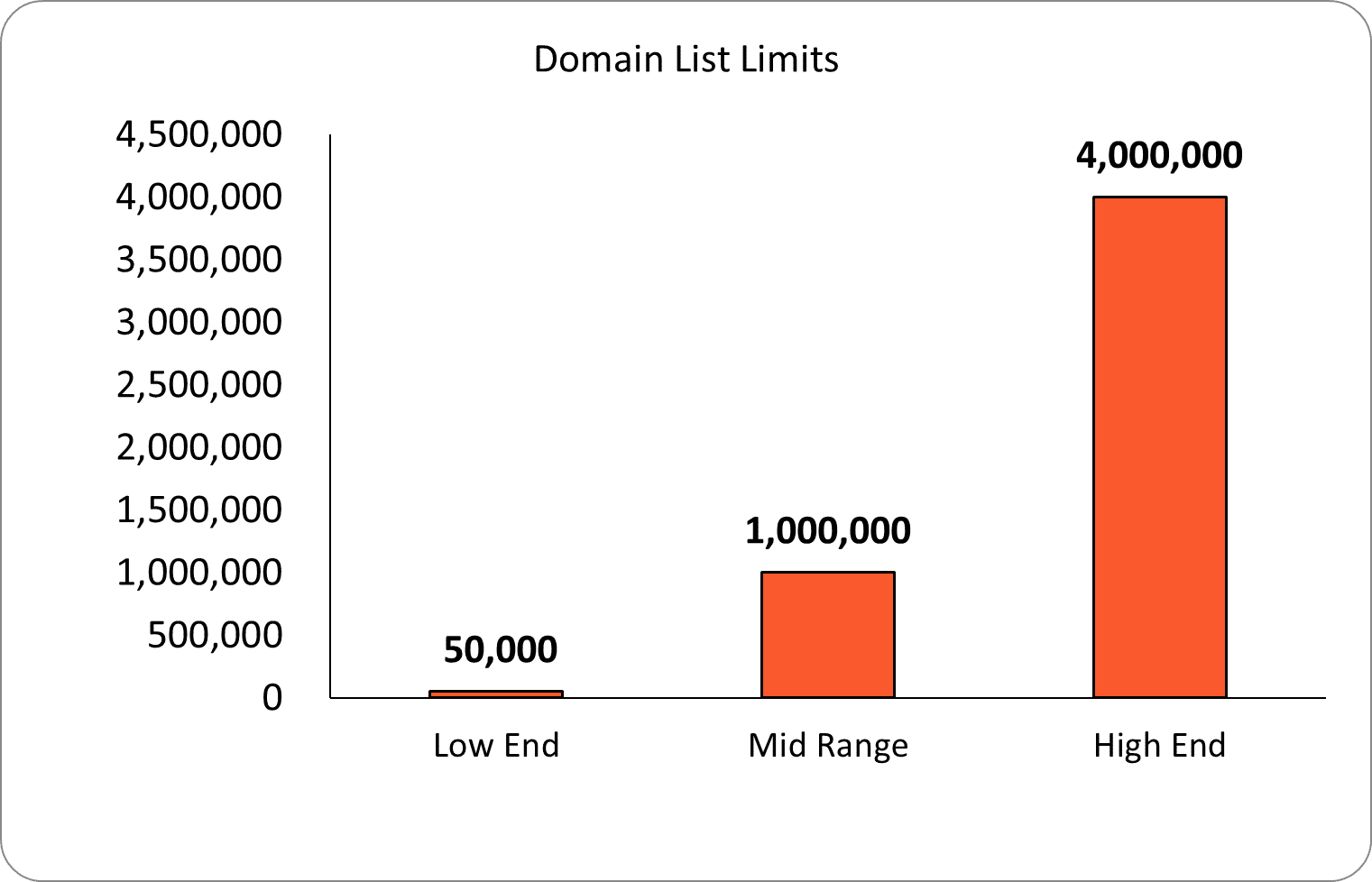
To put the volume limitations into perspective, below is actual data from one of the top next-generation firewalls on the market today.
As you can see depending on the size of the firewall, the volume of IP indicators you can use in its external blocklist ranges between 50,000 and 150,000 and the volume of Domain indicators ranges between 50,000 and 4 million.
To put these external blocklist indicator volumes into perspective, let’s take a look at two threat intelligence feed examples. The first is an IP reputation feed that has approximately 4 million indicators. The second is a malicious domain blocklist that has approximately 3.5 million indicators.
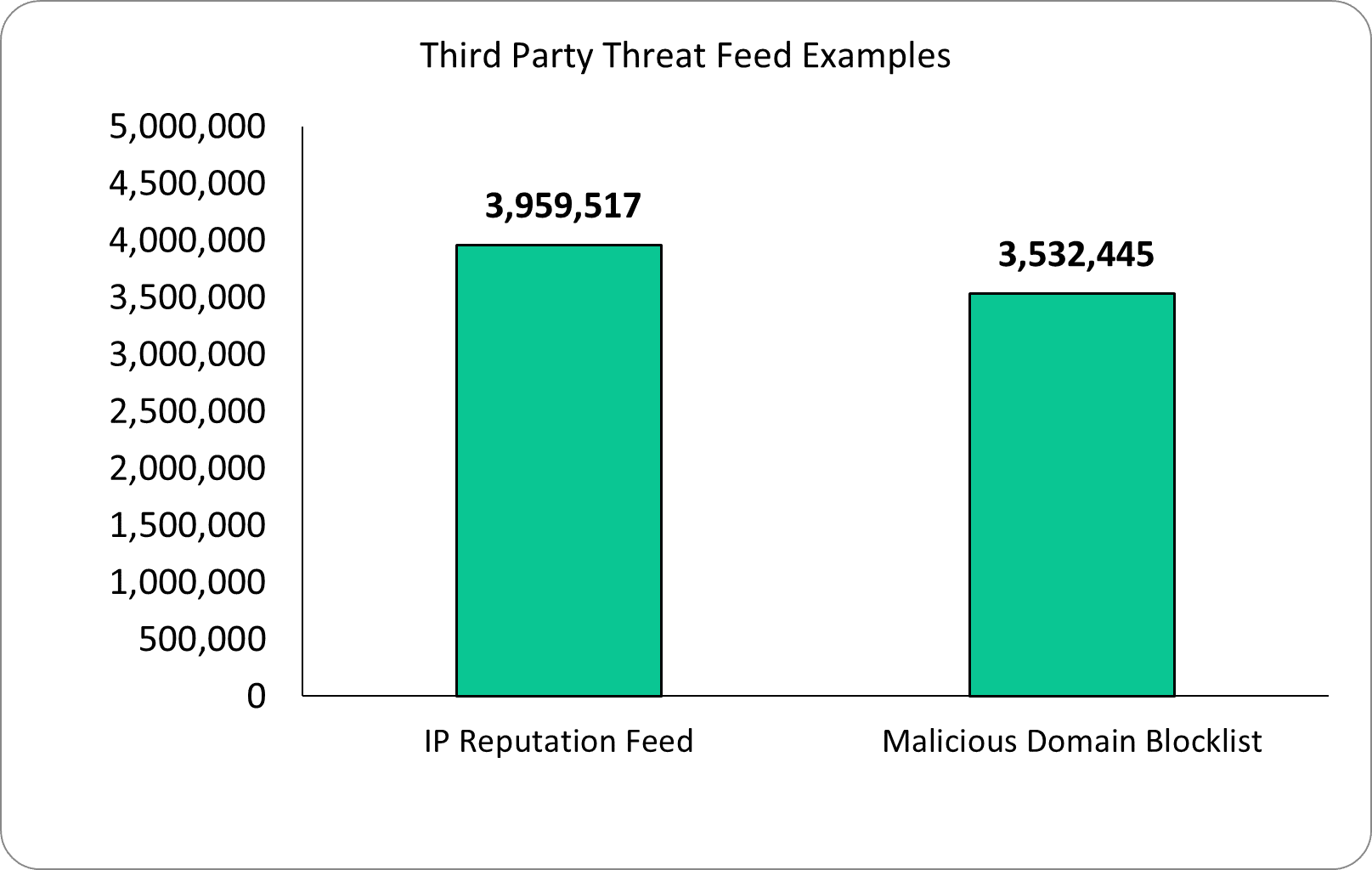
As you can see, trying to integrate these feeds into a firewall would be nearly impossible. As an interesting side note, for the IP reputation feed even if you reduced the feed to indicators with confidence scores of 95 and higher you still wouldn’t be able to integrate them into the firewall.
While firewalls have significant volume constraints using threat intelligence, they also have limited ways you can integrate data into them. For example, most firewalls only allow you to integrate threat intelligence into them via a text file that is accessible over HTTP/HTTPS. While this is a common way to integrate threat intelligence data, it is far too limiting. For example, many organizations use CSV files to create and manage their own internal block and allow lists. Integrating industry threat intelligence from ISACs/ISAOs often requires the use of a standard like STIX/TAXII. There’s also the fact that many organizations want the ability to integrate threat intelligence that is being generated by other security controls like SIEMs, Threat Intelligence Platforms, SOARs, and other systems.
The bottom line is that the ways you can integrate the small amount of threat intelligence you can add to a firewall are very limited.
To be fair, it’s not the firewall’s fault that it has limited ability to add threat intelligence from other sources. Firewalls were not designed to work with large volumes of third-party threat feeds. To take this a step further, as one cyber industry expert pointed out, firewalls were designed for stateful traffic inspection not volumetric packet dropping.
On top of this, firewalls do a gazillion different things today (that they also weren’t originally designed to do) all which require significant resources. This leaves little resources left to handle the processing of third-party threat intelligence data.
While it’s not the firewall’s fault, the reality is that the firewall gaps we’ve discussed so far pose a significant problem for organizations. The limited view of threat intelligence that firewalls use to detect and block threats combined with a limited ability to significantly increase the intelligence of your firewall means your network is only partially protected from today’s cyber threats.
In our next blog, we will look at the third firewall gap, which is that updating intelligence in firewalls is too manual and slow. After that, we will pivot and start looking at how Threater can help you fill the firewall gaps, improving not only the protection of your network but also the efficiency and effectiveness of your security operations and your firewall.