Firewall Gap #3: Updating Firewalls is Too Manual & Slow

In our previous blog, we took a closer look at the second firewall gap – the limited ability to add threat intelligence. These limitations included both the volume of threat intelligence you can integrate into a firewall and the ways you can integrate in it.
In this blog, we will focus on the third firewall gap. This gap is that updating intelligence in firewalls is too manual and slow. The result is more work and a time gap as far as your ability to detect and block threats.
For most organizations the process of managing threat intelligence in firewalls is manual and involves updating external blocklists directly on the firewall.
(If you are one of the fortunate ones to be using a Threat Intelligence Platform and/or SOAR, you can pass Go, collect $200, and jump to the next section because the volume limitations of firewalls create additional blocklist management challenges).
Many firewalls provide some automated blocklist capability with the ability to integrate a text file over HTTP/HTTPS. This allows you to maintain a single text file and have this automatically updated in your firewall(s).
While this provides some relief to the manual work and time spent managing threat intelligence in firewalls, it’s usefulness is limited to custom blocklists and integrating a few open source threat intelligence feeds. It’s not conducive to managing threat intelligence from many different sources.
On top of this, in many organizations, firewall changes are required to go through a change management process driven by compliance requirements. This adds additional time to updating blocklists.
The end result is that the manual and time consuming process of managing blocklists on firewalls creates a delay in your ability to rapidly respond to threats.
The threat intelligence volume of limits of firewalls combined with the dynamic nature of threat intelligence amplify these problems. The threat intelligence volume limits of firewalls require you to spend more time managing and optimizing blocklists. For example, you may be forced to age off indicators faster than you want to in order to make room for fresher threat intelligence.
Another challenge is the dynamic nature of threat intelligence. Threats are rapidly changing and so is threat intelligence. An IP that is classified as malicious right now might be deemed benign in a few minutes. Data from a blog by one of our partners, ThreatSTOP, provides a great illustration of this. It’s a snapshot of an open source threat intelligence feed. What’s interesting is that 66% of the indicators on the feed were on for 1 day or less.
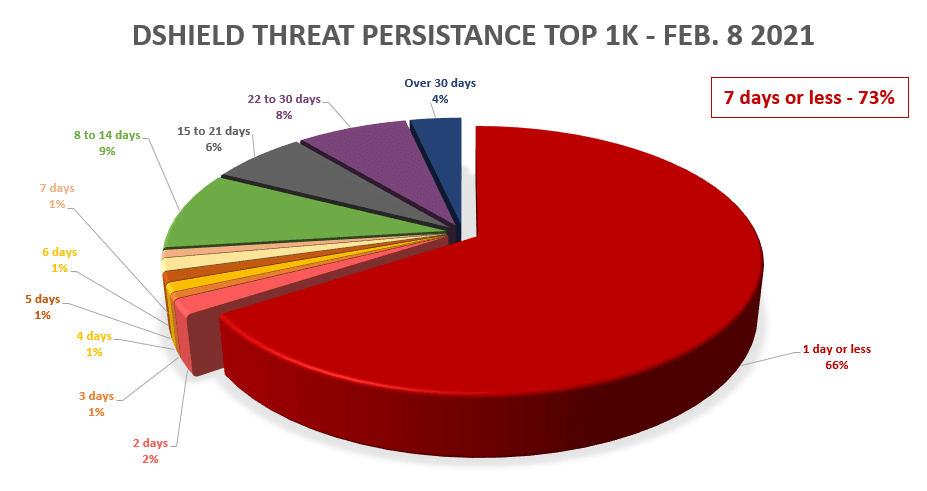
Source: ThreatSTOP Blog – How Long Does An IP Address Stay Infected? February, 9, 2021
The dynamic nature of threat intelligence makes it nearly impossible and impractical to manage it manually. No one has the cycles to spend constantly managing threat intelligence. Additionally, the dynamism and frequency of updates does not align well with a firewall update process that is governed by change management.
In the last few blogs, we’ve taken a closer look at three firewall gaps. To summarize:
In the next blog, we will shift our focus to how Threater can help you fill in the three firewall gaps enabling you to improve security, reduce manual work and save time all while making your firewall better in the process.