How Threater Fills the Firewall Gaps

In our last few blogs, we took a detailed look at three firewall gaps including: (1) They Don’t Catch Every Threat; (2) Limited Ability to Add Intelligence and; (3) Updating Intelligence in Firewalls is Too Manual & Slow. The result is a large gap in organizations’ cyber defenses and excess manual work and time spent managing threat intelligence in firewalls (i.e. managing external block and allow lists). In this blog, we will look at how Threater fills in the three firewall gaps allowing you to improve network protection, reduce manual work, and save time.
Firewalls don’t catch every threat because the threat intelligence they use represents too narrow a view of the threat landscape. Defending against threats is a volume game that requires the use of large volumes of cyber intelligence from multiple sources. No one source of threat intelligence or existing security control can cover the entirety of the threat landscape. This means it’s critical to use threat intelligence from multiple sources.
At Threater our strategy is 100% focused on partnering with threat intelligence providers. There is a wide range of threat intelligence available across a broad spectrum of providers including commercial threat intelligence providers, open source, government, and industry sources.
As part of our platform, we’ve sourced cyber intelligence from many leading sources. In fact, our platform uses over 30 different cyber intelligence sources to detect and block threats but also make it easy for you to allow traffic from known good sources.
One simple way to think about this is that with Threater, on day one, you have 30 sets of eyes detecting and blocking threats compared to the one pair of eyes your firewall uses. However, why stop there?
With a wide array of cyber intelligence available combined with the fact that organizations also generate their own valuable intelligence, it’s critical to have the flexibility to add more sources of intelligence. The challenge with firewalls, and their second gap, is they have limited ability to add threat intelligence. These limits include the volume of threat intelligence they can support and the ways you can integrate intelligence into a firewall.
Threater fills this firewall gap by being able to support a massive volume of threat intelligence data and by giving you multiple, easy ways to integrate threat intelligence data from any source into the platform.
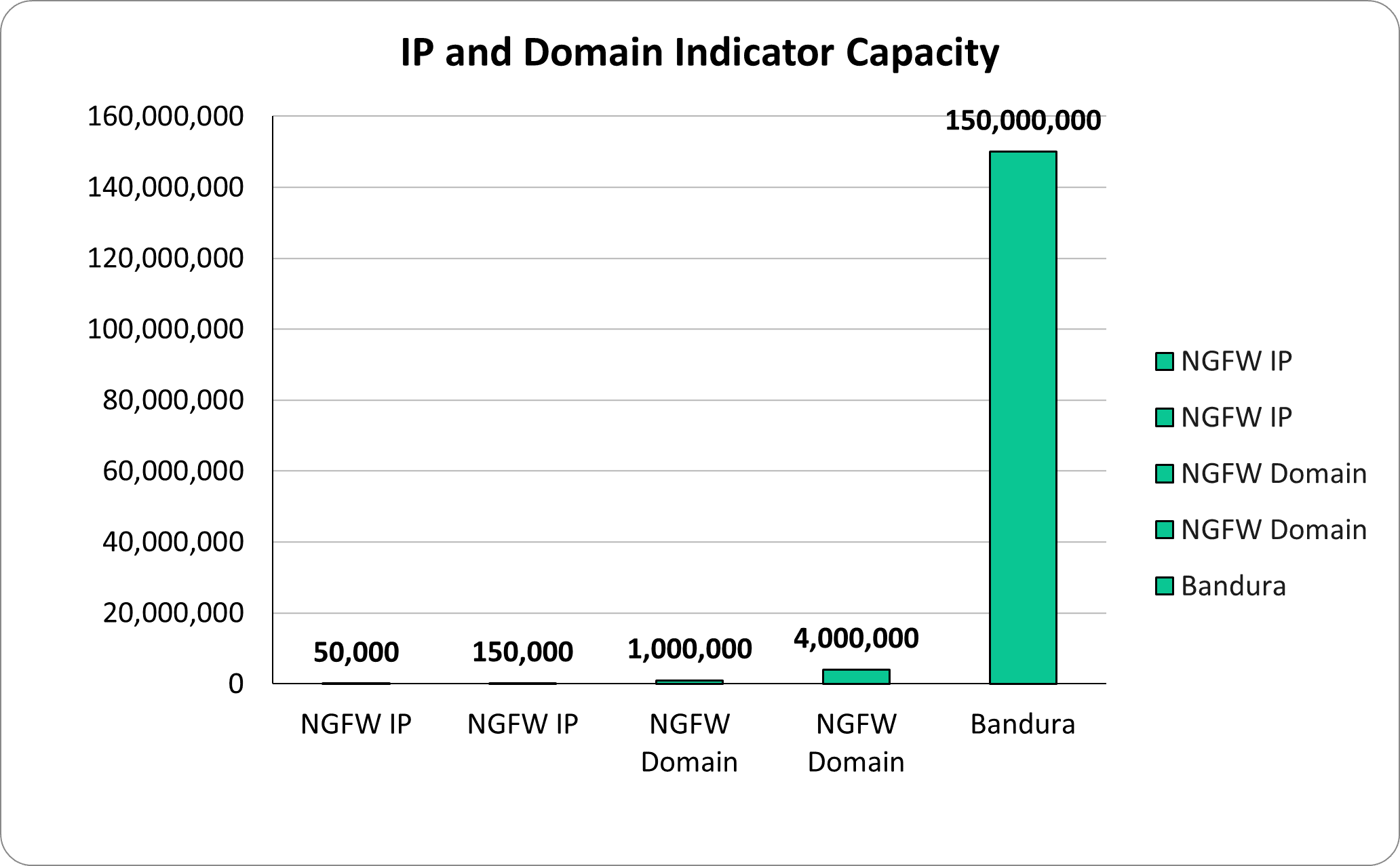
From a volume perspective, the Threater platform can handle up to 150 million IP and domain indicators, which far exceeds what any firewall can handle.
The Threater platform also has multiple mechanisms that allow you to easily integrate threat intelligence into the platform. These include:
In summary, Threater eliminates the second firewall gap by allowing you to easily add intelligence into the platform at a scale you can’t do with a firewall.
The third firewall gap is that updating intelligence in firewalls is too manual and slow. For many organizations managing external blocklists and allowed lists on firewalls continues to be a manual process. The threat intelligence volume limits of firewalls adds more work and time and even more time can be added due to firewall change management processes.
Threater fills the third firewall gap through a combination of automation, speed, and scale. Threater lets you automate threat intelligence and external blocklist management. For example, all of the integration mechanisms we just discussed are automated. This means that after an initial, simple configuration the cyber intelligence that is integrated into the platform is automatically updated. The result is less manual work, time savings, and improved protection as you are always operating with the latest intelligence and you can more rapidly respond to threats.
Speaking of speed, many Threater customers highlight their ability to more rapidly respond to threats because changes in Threater are not required to go through a time-consuming, firewall change management process.
The scale at which the Threater platform can handle threat intelligence also plays an important role in filling this gap. The threat intelligence volume limitations of firewalls have downstream impacts when it comes to managing intelligence in firewalls. The highly dynamic nature of threats and threat intelligence means more manual work and time spent managing blocklists. It also means that you are only able to use a subset of available intelligence leading to suboptimal protection. For example, a Threater customer pointed to having to age off indicators from their blocklists more rapidly than they wanted to do as a result of firewall blocklist volume limitations.
Overall, through a combination of automation, speed, and scale, the Threater platform fills the third firewall gap. The result is less manual work, time savings, faster threat response, and improved network protection.
In the previous blogs, we discussed the three firewall gaps: (1) firewalls don’t catch every threat; (2) firewalls have limited ability to add intelligence; and (3) updating threat intelligence in firewalls is too manual and slow. In this blog, we showed you how the Threater platform fills in each of these gaps. With Threater you can: