Test Drive Valuable Cyber Intelligence in Marketplace
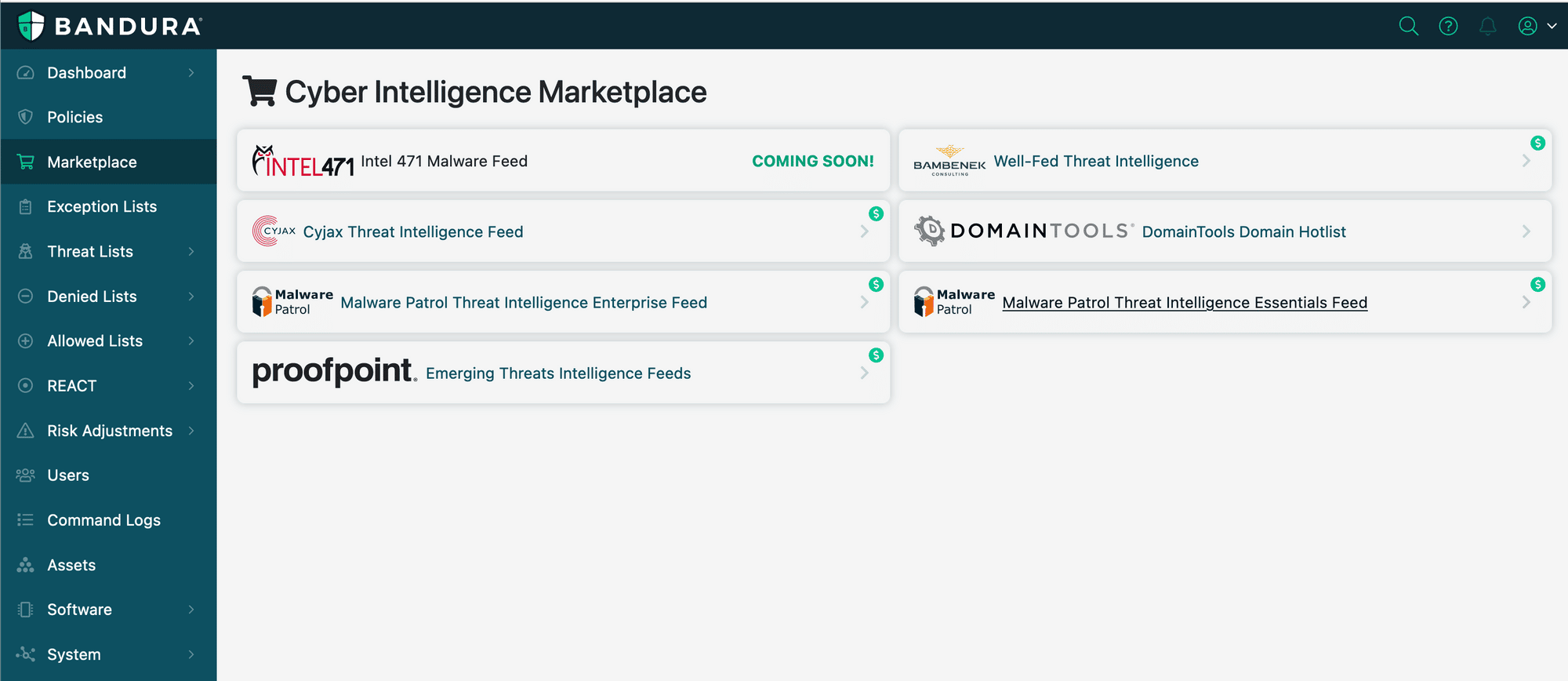

A few months ago, we launched our Cyber Intelligence Marketplace. At Threater, we believe that defending against cyber threats is a volume game that requires the use of massive volumes of cyber intelligence from multiple sources. These sources include commercial threat intelligence feeds, open source intelligence, industry, and government threat intelligence.
The goal of Cyber Intelligence Marketplace was simple – provide our customers with additional, valuable cyber intelligence data options to help them better protect their networks from cyber threats. Today, the marketplace has a mix of free (DomainTools) and premium cyber intelligence feed options (Bambenek, Cyjax, Intel 471, Malware Patrol, and Proofpoint).
When we launched the marketplace, a common question we got from customers was “is there a way to evaluate the feeds to see the value they have in my environment?”
The great news is the answer is now yes!
We’re pleased to announce that a Free Trial capability is now available in the marketplace. The Free Trial capability allows customers to try any premium feed for 7 days.
Here’s how easy it is to sign up.


That’s it!
Within minutes, the cyber intelligence feed you selected will be available for activation in the Threater app. Simply enable the feed in your Denied Lists (IPv4 and/or Domain) and make sure it’s enabled in your policies.
Once a feed is active and enabled you can easily assess the protection value it is providing for your environment by reviewing your Threater logs. Threater logs provide threat source attribution which provides information on which cyber intelligence feed source(s) and indicator is on.
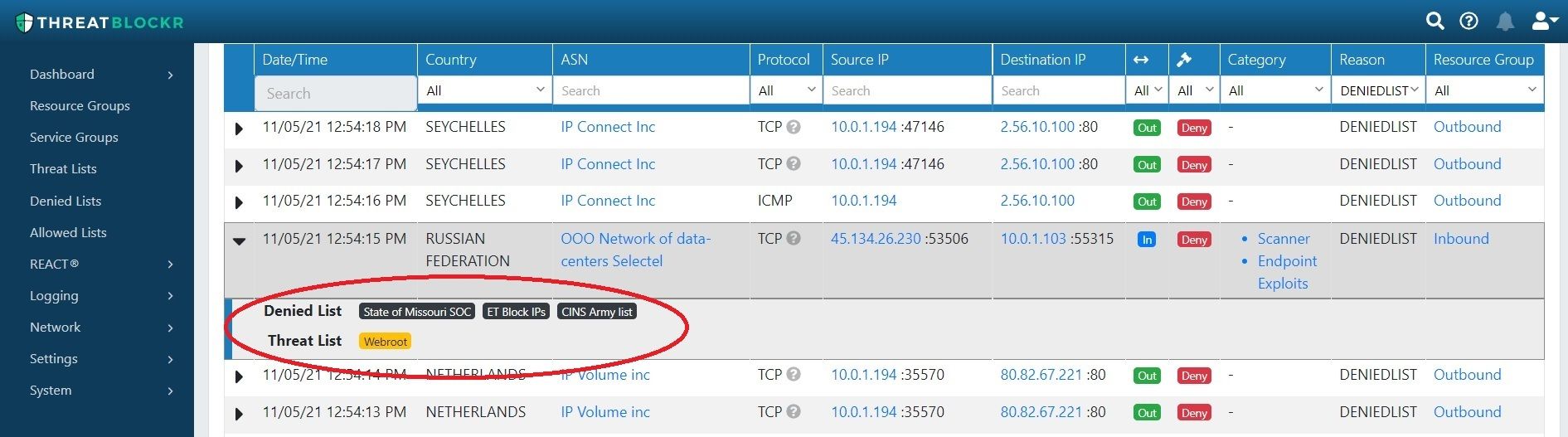
Defending against cyber threats is a volume game that requires the use of massive volumes of cyber intelligence. Cyber Intelligence Marketplace provides Threater customers access to additional cyber intelligence feeds that can further strengthen protection from cyber threats.
We encourage Threater customers to take advantage of our Free Trial capability and try one or more feeds today!