Blog – September 04, 2025
threatER Announces Support for TLS Secured Syslog Export (RFC5425)
The Product Development team at threatER takes great pride in delivering quality features that provide value to our customers. One feature that has been in our backlog for a while is the capability to export TLS (Transport Layer Security) encrypted syslog messages from threatER Enforce deployments as defined in RFC5425.
threatER Enforce has long supported the export of unencrypted RFC5424-compliant messages. The feature has allowed customers to safely send logging information on local administration networks, and then make use of third-party tools to ingest, store, and analyze how the Enforce software has applied policy driven threat intelligence to inbound and outbound traffic. Now, customers have the capability to do all of the above—but securely, such that they are no longer specifically limited to local admin networks.
The following blog post will outline some of the specific logging improvements we have recently made to the Enforce export logging feature that should make customer adoption easier, as well as improve log message transfer reliability and security. All of the new export capabilities below apply to both our traditional Enforce product as well as the new WiFi product offering. Keep in mind that we have preserved the existing mode of operation for customers content with their existing logging arrangement so there is nothing they need to do—any previous export log settings are preserved. The new TLS feature is automatically presented in threatER Portal as an additional option when Enforce instances are upgraded to build 284 or later.
Lower Barrier to Customer Adoption
Traditionally running on low-cost hardware with limited system resources, the Enforce software is not intended to serve as a non-volatile or high volume log storage tool. For traditional Enforce deployments, the number of log entries that can be stored on the device will depend on the amount of RAM installed on the host. In high bandwidth deployments with limited RAM, this may result in only a few hours worth of log retention. Furthermore, all log history is lost when the host is powered off. For WiFi deployments the on-device log retention is even further limited due to even fewer resources being available. Without a rich log history to work with, our Customer Success team is often severely constrained when assisting customers that are unable to provide any log history.
Many of our customers are small businesses that don’t have the technical expertise to configure a syslog server on their local admin networks capable of ingesting log messages (say, syslog-ng or OpenObserve, for example). Furthermore, transmission of unencrypted “clear-text” payloads to cloud-based services is a really bad idea. Until now, customers that wished to securely export Enforce logs to cloud based services were required to effectively “proxy” unsecure Enforce log messages via an additional co-located system to ensure the messages were TLS secured before transit over a public network. Needless to say, convincing these customers that they need to procure some additional equipment and configure some third-party software has been a challenge.
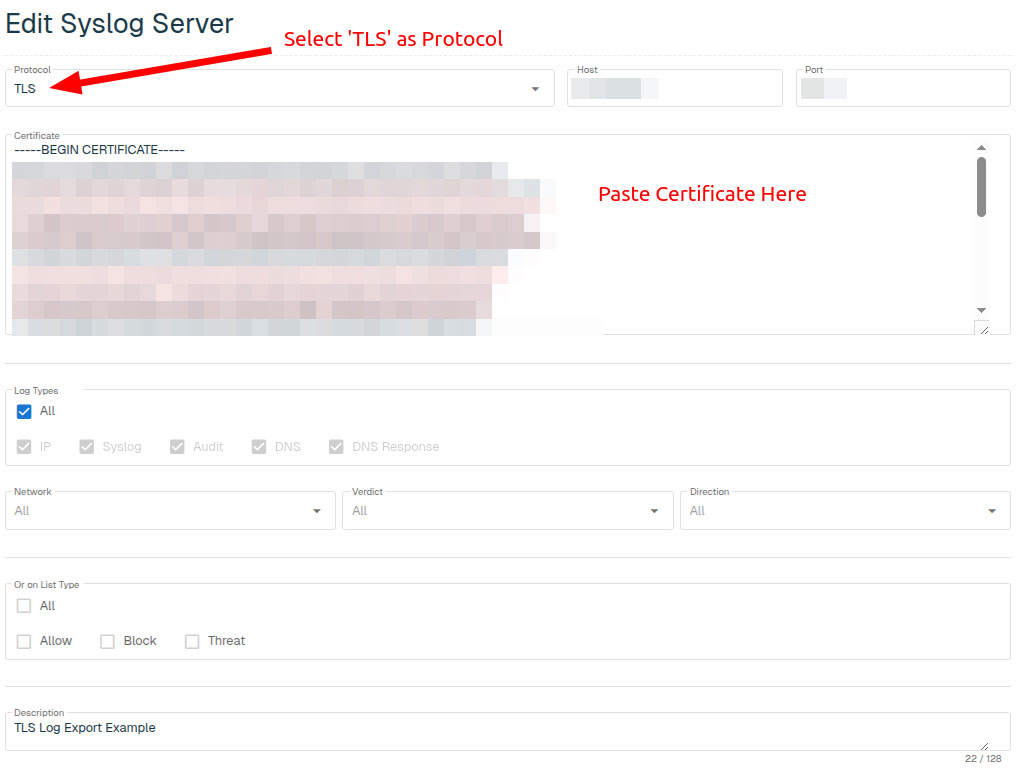
Now, with the Enforce software capable of natively securing exported log messages via TLS, customers can easily and securely transmit Enforce logs directly to cloud-based syslog services of their choice. Once the desired third-party syslog service is up and running, all that is required is to configure the syslog server host (IP or domain name) and provide a matching TLS server certificate. Furthermore, all Enforce syslog configuration is performed via the threatER Portal; there is no need to be on site to make changes to any of the Enforce syslog export settings. This remote management capability via threatER Portal makes syslog configuration changes much easier, especially for our customers that have multiple Enforce deployments that are geographically distributed. Figure 1 below demonstrates the new threatER Portal controls that enable TLS secured export.
Improved Message Delivery Reliability
Until now, the Enforce software was only capable of utilizing UDP as a transport layer protocol for exported syslog messages. Most folks are probably already aware that UDP alone has no built-in security or retransmission mechanism. Therefore, the use of UDP datagrams to transfer syslog messages cannot guarantee message delivery, and message loss can occur without notification. Fortunately, the use of TLS which is underpinned by TCP, does provide these features. As such, in addition to providing for secure transfer, the use of TCP/TLS is always going to be superior to UDP from a reliability perspective.
In addition, we have included a non-secure TCP mode of operation for customers who want the reliability of TCP log message transfer but are certain they don’t require a TLS-encrypted connection. This might apply to customers that have a co-located syslog server and don’t want the hassle of obtaining or generating CA certificates. However, we always recommend the use of TLS even if that means generating a self-signed certificate. Generating a self-signed certificate is simple to do and there are many online guides available that demonstrate how.
Summary
The new features outlined above will allow threatER Enforce customers to export Enforce RFC-compliant messages more securely and reliably. Customers that are currently utilizing the unsecure legacy UDP export mode will probably benefit by switching to the new TLS secured mode. For customers that are not leveraging export of RFC-compliant log messages this would be a great time to reevaluate doing so. We strongly encourage all customers to export their Enforce logs to the syslog server or cloud service of their choice and always secure the connection with TLS.

