Statement on the FBI’s Cyber Attack Warnings Impacting Healthcare


Updated: 3 November 2020 1:00 PM ET
On October 28th 2020, the FBI, in conjunction with HHS and CISA, issued an imminent cyber attack ALERT on the National Cyber Awareness System regarding a potentially crippling Ransomware campaign that is being launched against the US Healthcare system.
Threater recommends the following immediate steps be taken on your Threater appliances to help protect your network from these impending attacks:
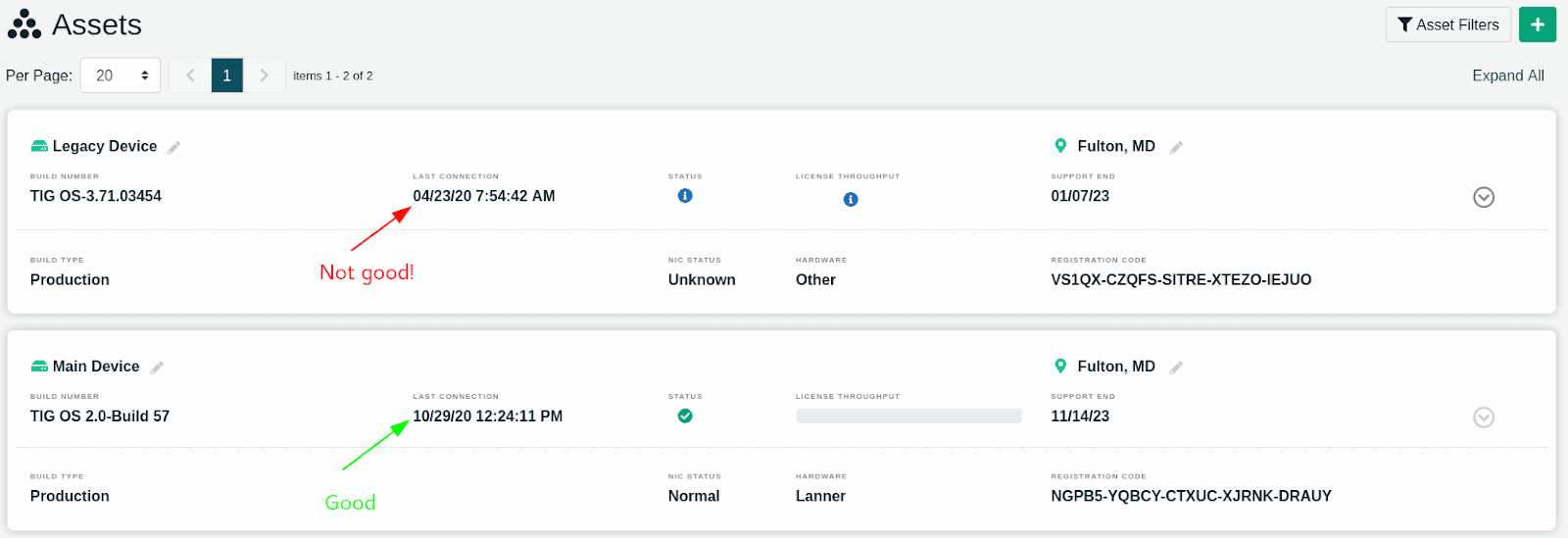
1) Confirm that each of your Threater appliances is actively connecting to GMC: This will ensure that your appliances are armed with the most up-to-date threat intelligence. To ensure connectivity, navigate to the Assets page in GMC. For each Threater appliance you will see a “Last Connection” field (see image). A “dash” will mean that your Threater appliance has never connected to the GMC and will likely need to be registered with the GMC. If the Threater appliance is actively connected you should see the Date/Time reflect very recently (within the past 15 minutes). If you see an older Date/Time, it may be an indication that your Threater appliance is not actively connected.
If you need help, please contact us at support@threater.com.
2) Confirm that all of your Threat Feeds are Enabled:
We encourage you to review the out-of-the-box IPv4 and Domain Denied Lists. Ensure that you have enabled the appropriate denied lists. Specifically, there are 4 new Healthcare focused Denied Lists available via GMC. These four new lists are DISABLED for our current customers* but can easily be enabled and added to existing policies in the GMC. The details are as follows:
US-CERT Healthcare Ransomware – List of IP IOCs published by the CISA, FBI, and HHS (IPv4 denied list)
Threater Healthcare Ransomware – List of IP IOCs curated by Threater (IPv4 denied list)
US-CERT Healthcare Ransomware – List of domain IOCs published by the CISA, FBI, and HHS (domain denied list)
Threater Healthcare Ransomware – List of domain IOCs curated by Threater (domain denied list)
*Note that for new customers these lists will be enabled by default in the Denied Lists
Note that COVID-19-DomainTools-70 and COVID-19-DomainTools-99 threat feeds are free, out-of-the-box domain lists made available by DomainTools to our customers. The terms ‘70’ and ‘99’ that appear at the end of the list names are confidence factors supplied by DomainTools, the leading domain threat intelligence provider. 70 indicates that DomainTools is at least 70% confident in their assertion that those list entries are malicious, and 99 means that they are at least 99% confident.
We recommend that you enable at least COVID-19-DomainTools-99.
For a more aggressive profile, you can also enable COVID-19-DomainTools-70.
If you happen to receive false positives from any domain list, you can easily bypass the domains in an allowed list. If you need further assistance, please contact us at support@threater.com.
For Customers with Enterprise Subscriptions: For those of you with Enterprise Subscriptions, ensure that both Proofpoint Emerging Threat Feeds and DomainTools Malicious Domain Blocklist threat feeds are enabled and up-to-date. If you are currently on a Standard subscription and would like to upgrade to increased protection using these industry leading threat feeds, please contact us at sales@threater.com.
3) Enable GEO-IP Blocking: Ensure that your GEO-IP Blocking is enabled. As suggested by the FBI alert, these threat actors are operating in Eastern Europe. Threater suggests blocking Eastern European countries. As a best practice, Threater recommends blocking any country with which you know that you don’t need to do business.
4) Enable the H-ISAC (Health Information Sharing and Analysis Center) Industry Specific Threat Feed: If, as a member of the healthcare industry, you are a member of H-ISAC, then you can import the API key provided by H-ISAC into our H-ISAC plugin. The H-ISAC feed is a specifically tailored feed for the healthcare industry. For more information about H-ISAC and becoming a registered H-ISAC member, please see their excellent website and related resources at: https://h-isac.org/.
The following instructions are for those customers who are already H-ISAC members: First, you’ll want to make sure you have your H-ISAC username and password credentials on hand. If you don’t know them, please reach out to H-ISAC for assistance (see link above).
To set up the feeds, log into your GMC account and select Denied List and then IPv4 from the left menu. On the IPv4 Denied Lists page, click on the green + icon in the upper right. Select “H-ISAC IPv4 Lists” in the Type dropdown on the Create IPv4 Denied List modal. The most important thing is to enter the correct Feed Name. While H-ISAC members are allowed to create custom feeds, there are also several main feeds available to you:
a) system.Default – contains all information available to members at the TLP Amber, Green, and White since June 8 2016. Note: this is a large amount of data!
b) system.NH-ISAC-Members-Amber-All – H-ISAC Members only data at a TLP Amber level
c) system.NH-ISAC-Green-All – Data classified at the TLP Green level
d) system.NH-ISAC-Amber-Green-White-All – Data classified as Amber, Green, or White
e) system.Test-24-Hour – 24-hours of TLP Amber data for testing purposes
Details on the Green, Amber, and White feeds are available at https://h-isac.org/h-isac-tlp-definition/.
Once you have entered the feed name, give your list a name (such as “H-ISAC Amber All”). The description field is optional, and can be used at your discretion. For the Interval in Minutes, we recommend this be set to 60 minutes for all feeds except “SYSTEM.DEFAULT”, which H-ISAC requests be set to no less than 720 minutes due to the size. Enter the value 720 for TTL Hours (for all feeds). Lastly, you’ll want to set Authentication Type to Basic, and provide your User Name and Password credentials.
REMINDER: This attack is IMMINENT. This means that Government sources have determined that a credible Ransomware attack is being launched by Eastern European threat actors. For more information on mitigation suggestions and the FBI, HHS, CISA alert, go here: https://us-cert.cisa.gov/ncas/alerts/aa20-302a
As more information becomes available, we will post any updates to our blog.