Gravwell Integration with Threater
The combination of Threater & Gravwell provides joint customers with a comprehensive approach to cybersecurity that combines actionable threat intelligence with powerful data analytics capabilities.
Threater blocks known bad traffic at scale using a combination of simple, innovative technology and best-in-class threat intelligence. Gravwell’s Data Fusion Platform enables users to easily ingest, store, analyze, and display machine data, including security logs.
The combination of the two platforms provides improved protection from cyber threats and more effective and efficient threat detection, investigation, and response.
Benefits
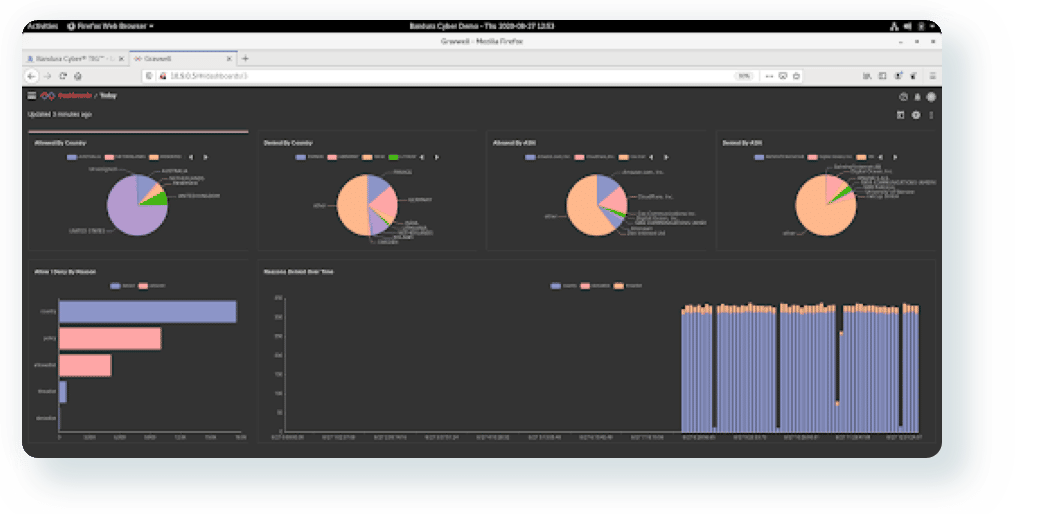
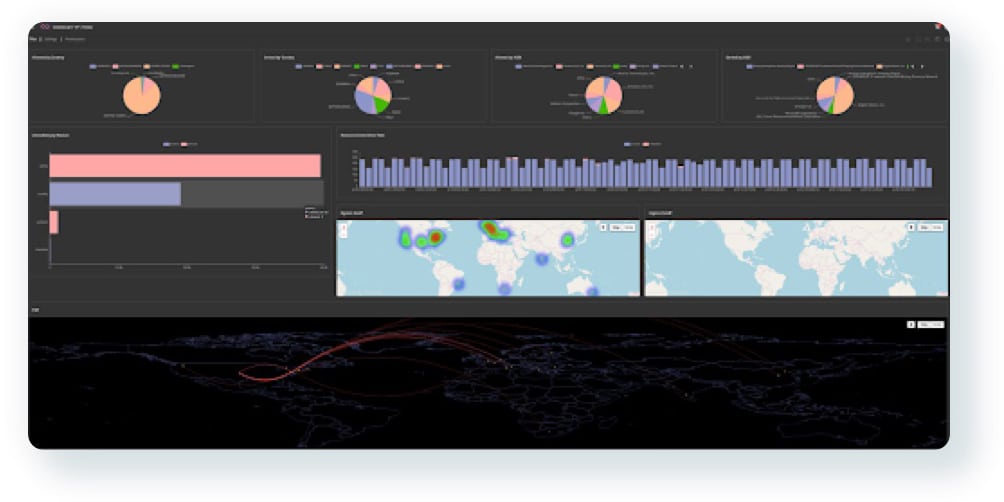
Comprehensive visibility into your security posture.
Improve threat detection.
Reduce the time to investigate and respond to security incidents.
Features
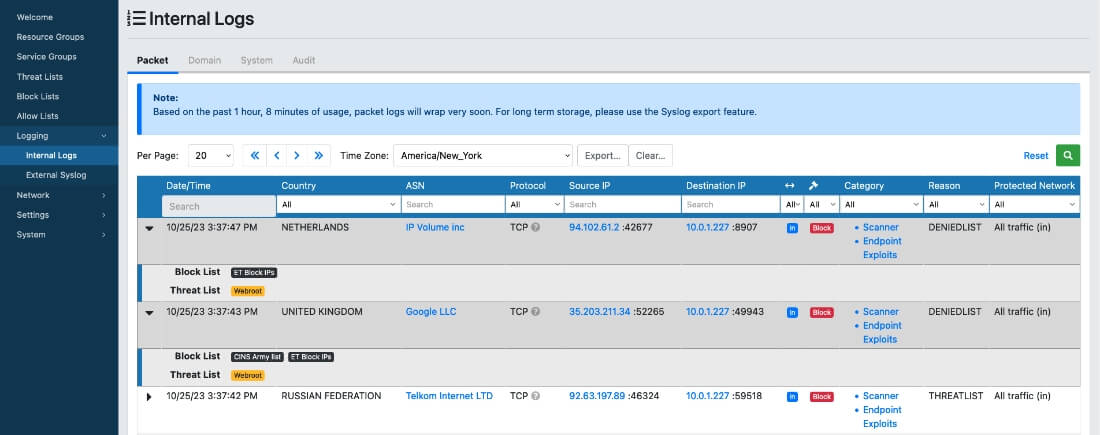
Leverage Gravwell for longterm storage of Threater logs.
Aggregate logs from multiple Threater appliances in Gravwell.
Use more customizable and advanced analytics, visualization, and reporting capabilities.
Correlate Threater logs with logs from other security controls and systems.