ThreatConnect Integration with Threater
ThreatConnect and Threater have joined forces to make threat intelligence more actionable, automated, and scalable.
Threater and ThreatConnect have partnered to make threat intelligence more actionable, automated, and scalable. This powerful integration enables organizations to strengthen network defense by proactively using threat intelligence from ThreatConnect and the Threater platform to block IP and domain-based threats before they hit your network.
The ability to take action on threat intelligence is critical to maximizing its value. However, organizations often face challenges integrating threat intelligence into traditional network security controls like firewalls. Most firewalls have limited capacity to integrate third-party threat intelligence indicators, and managing external blocklists in firewalls is complex and time consuming.
Benefits
Strengthen network defense by taking action with ThreatConnect threat intelligence to prevent inbound and outbound connections involving malicious IPs and domains.
Reduce staff workload by automating IP and domain block listing at scale.
Maximize threat intelligence ROI by making it actionable and increase the ROI and efficiency of existing nextgeneration firewall investments.
Features
Threater integrates threat intelligence from various sources to block up to 150 million known malicious IPs and domains before they hit your network.
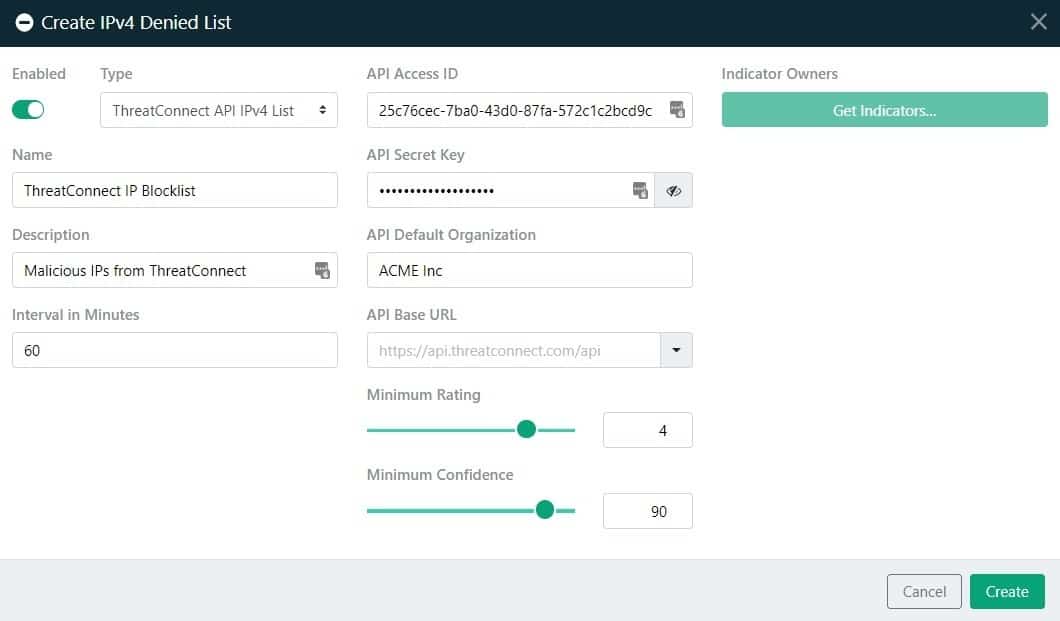
Curated, relevant intelligence from ThreatConnect is automatically synchronized to the Threater platform, ensuring always-current network protection and eliminating manual efforts.
Threat intelligence-driven context from the network edge via the Threater platform enhances the value of ThreatConnect threat intelligence with visibility into malicious IP and domain activity on your network.