©Threater 2024
Deployment Options
Threat actors don’t care where your network is. (Luckily, neither do we.)
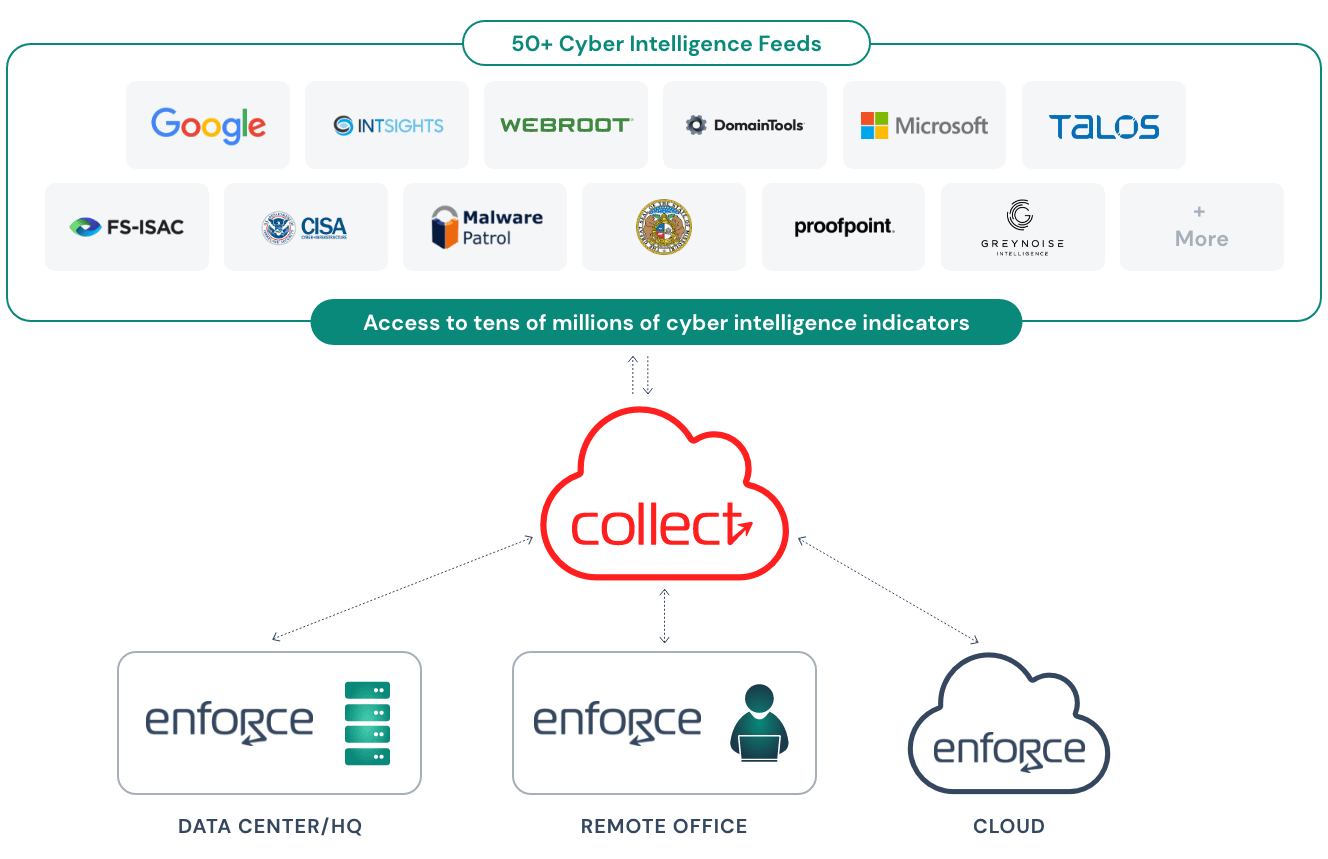
Data Center/HQ
Threater Enforce sits in line with your security stack, blocking traffic to and from known threat actors at line speed. Threater works with all other security technologies to help reduce redundant alerts and deploys in about 30 minutes.
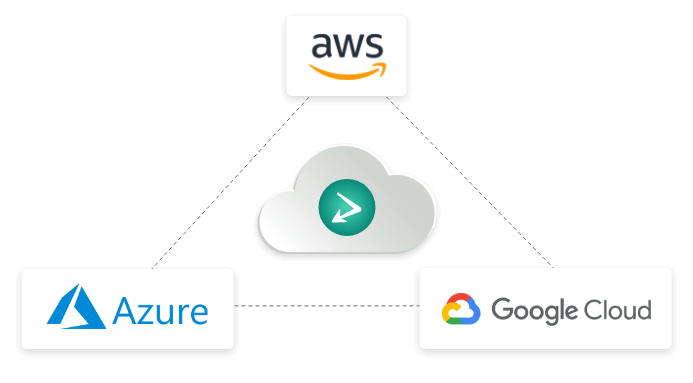
Cloud
By leveraging Gateway Load Balancers, Threater cloud deployments in AWS, Azure, and Google Cloud work exactly the same way as on-premise deployments. That means no separate code bases, no update lags, with no exceptions. Whether you are running on IntelAMD or ARM you will be able to deploy Threater anywhere and everywhere.
Remote
Have a more complicated network setup? No problem. Threater will work with you and deploy wherever you are to make sure your network is automatically blocking traffic to and from known threat actors.